In this blog post, I will be taking you through how to make use of the “--tamper” parameter of the SQLMap tool to bypass the limitations of a web application using JWT tokens.
A function of web applications that use JWT tokens is to make the token expire after a certain period of time. This then results in you receiving an error 401 message in the web application, meaning that you don’t have the correct privileges to use that specific web application or endpoint.
During a recent assessment, I came across a web application, which made use of JWT tokens for its authentication process. After token expiry, a request should always be sent to the application to reauthorise access and get a new token.
When using SQLMap to test a web application against potential SQL injection vulnerabilities, this became an issue, as the application would re-authenticate and a new token was issued, which would then result in an error 401 message.
I came up with a solution to this problem when using SQLMap, by requesting a new token and then changing the authorisation header which would then result in this problem being bypassed.
Below is the example of how this was successfully achieved.
First the request for a new token was sent to the application:
As can be seen below, this request then responded back with JSON, containing an “access_token” which could then be used in the next request:
For the next step, I then used Python to recreate the POST request in a script. In the screenshot below, you can see the code that was used for the POST request:
In addition to the above code, the authorisation header should be rewritten with new information before every request that is sent by SQLMap, as can be seen below:
The full tamper script should then look like the code in the screenshot below:
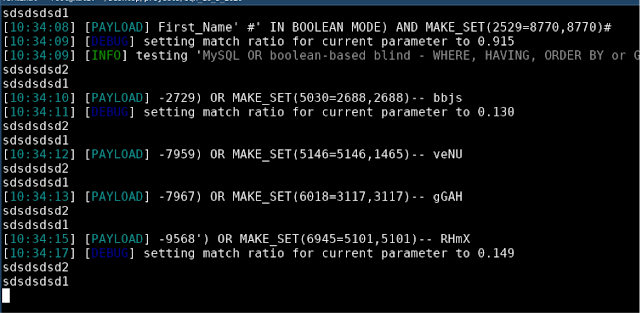
Lastly, in the screenshot below you can see the command for executing the tamper script against a target using SQLMap(sqlmap -u https://url.com/ --tamper bypass.py):
At this point, requests are sent correctly by refreshing the token and you will no longer receive a 401 error message.
I hope you have found this information to be of a value and that it will assist you in future penetration tests.
- Blog post by Motaz of Telspace Systems.
- Blog post by Motaz of Telspace Systems.





No comments:
Post a Comment